Did you know that WordPress sites are a prime target for hackers? With over 60% of website owners using WordPress, it’s no surprise that cyber criminals are constantly on the lookout for vulnerabilities to exploit. If you’re running a WordPress site, the threat of getting hacked is real and can cost you dearly in terms of lost data, compromised customer information, and damage to your brand’s reputation.
But don’t worry, securing your WordPress website from hackers is entirely possible. As a seasoned web designer with 18 years of experience in WordPress Website Development and a track record of creating high-performing websites for clients across various industries, I’ve learned a thing or two about keeping WordPress sites safe and secure.
In this blog post, we’ll share some proven ways of securing a WordPress Website from hackers. From implementing the right security plugins and keeping your software up-to-date, to hardening your WordPress configuration and following basic security protocols, you’ll learn practical steps to minimize your risk and protect your online presence.
Ways of Securing a WordPress Website
1. Choose a Secure Host
Why Choosing a Secure Host is Important
Choosing a secure host is crucial for business websites because a data breach can have devastating consequences. According to a study by IBM and the Ponemon Institute, the average cost of a data breach in 2022 was $4.35 million, representing a 2.6% increase from the previous year. A secure host can help mitigate the risk of such costly incidents by implementing robust security measures and providing a secure environment for websites to operate.
How to Select a Trustworthy and Secure Web Host
- Research and evaluate potential hosting providers based on their security track record, certifications (e.g., ISO 27001, SOC 2), and implemented security measures.
- Look for hosts that offer features like regular security updates, malware scanning, firewalls, SSL/TLS certificates, and DDoS protection.
- Consider managed WordPress hosting services, as they often have specialized security measures in place for WordPress websites.
- Verify the hosting provider’s uptime guarantee and customer support responsiveness, as these factors can impact your website’s availability and security incident response.
Real-life Example:
In 2018, Equifax, one of the largest credit reporting agencies, suffered a massive data breach that exposed the personal information of over 147 million consumers. The breach was attributed to a vulnerability in their web application software running on an unsecured web server. This incident underscored the importance of choosing a secure web hosting provider that prioritizes security measures and maintains robust infrastructure.
2. Use Two-Factor Authentication (2FA)
What does 2FA mean and how it adds an extra layer of security beyond passwords:
Two-factor authentication (2FA) is a security measure that adds an extra layer of protection beyond traditional passwords. Instead of relying solely on a password, 2FA requires a second form of authentication, typically a one-time code sent to the user’s mobile device or generated by an authentication app. This second factor makes it much harder for unauthorized individuals to gain access, even if they have obtained the password.
Why weak passwords are vulnerable and how 2FA mitigates this risk.
Weak or easily guessable passwords are a significant vulnerability, as they can be cracked by brute-force attacks or exploited through data breaches. Even strong passwords can be compromised if they are reused across multiple accounts or obtained through phishing attempts. By implementing 2FA, even if an attacker manages to obtain the password, they would still need access to the second authentication factor, significantly reducing the risk of unauthorized access.
How to set up 2FA in wordpress:
- Install and activate a reputable 2FA plugin, such as “Google Authenticator” or “Two Factor Authentication” by WPBeginner.
- Configure the plugin to require 2FA for all user accounts, especially those with administrative privileges.
- For each user, follow the plugin’s setup process, which typically involves scanning a QR code or entering a secret key into an authentication app (e.g., Google Authenticator, Authy) on their mobile device.
- Ensure that all users have successfully set up their 2FA method and understand the process of entering the one-time code during login.
- Regularly review and update the 2FA plugin to ensure compatibility with the latest WordPress version and security best practices.
Example: According to a study by Microsoft, enabling 2FA can block over 99.9% of automated attacks and 66% of targeted attacks. This underscores the effectiveness of 2FA in preventing unauthorized access attempts.
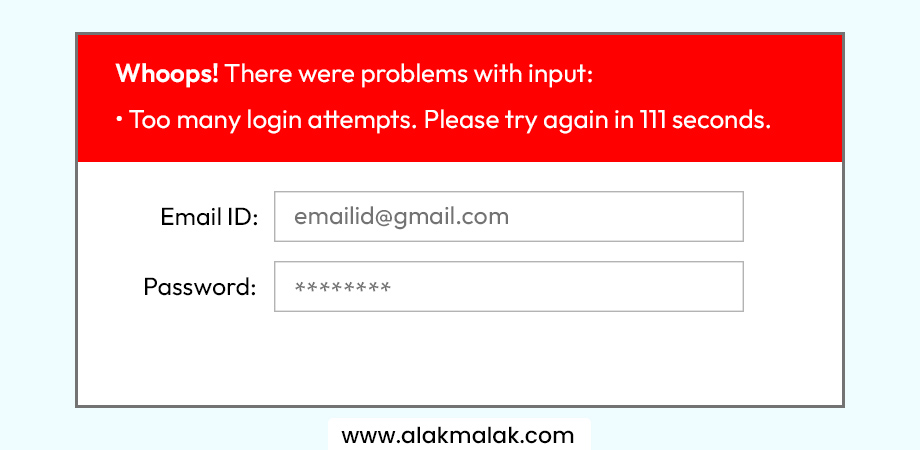
3. Add Brute Force Attack Protection
Brute force attacks are a type of cyber attack where an attacker attempts to gain unauthorized access to a system or account by systematically trying multiple combinations of usernames and passwords. In the context of WordPress, brute force attacks target the login page, trying to guess the correct credentials through automated scripts or tools that rapidly cycle through different password combinations.
Limit Login Attempts: Thwarting Persistence with Prevention
The good news is, brute force attacks can be thwarted by implementing login attempt limits. These restrictions block access after a predefined number of unsuccessful login attempts. This disrupts the automated guessing process and significantly reduces the risk of unauthorized access.
Here’s how you can put this security measure in place:
- Security Plugins: Several free and premium WordPress security plugins offer login attempt limitation features. Popular options include Wordfence Security, Limit Login Attempts Reloaded, and Sucuri Security. These plugins provide user-friendly interfaces for configuring the number of allowed attempts, lockout durations, and IP address blocking.
- Web Hosting Security Features: Many web hosting providers offer built-in security features that include login attempt throttling. Look for options within your hosting control panel to manage these settings.
Remember: When setting login attempt limits, find a balance between security and user experience. Too few attempts can be frustrating for legitimate users, while too many attempts can leave your site vulnerable. Start with a reasonable limit (e.g., 3 attempts) and adjust based on your website’s traffic and security needs.
Example: A popular e-commerce store running on WooCommerce experienced a significant spike in failed login attempts, indicating a brute force attack attempt. After implementing a security plugin with brute force protection features, they were able to block over 50,000 malicious login attempts within a week, ultimately preventing unauthorized access and potential data breaches.
4. Scan for Malware and Security Issues
Your WordPress website is a valuable asset, but it can also be a target for malicious actors who plant malware. Just like a virus infects your computer, malware can infect your website, causing a range of problems. Let’s explore the dangers of malware and how to scan for it effectively.
Dangers of Website Malware:
Malware can wreak havoc on your website’s functionality and reputation. Here’s how:
- Data Breaches: Malicious code can steal sensitive information like user login credentials, credit card details, or contact forms. This can lead to identity theft and financial losses for your users, damaging your website’s trust.
- SEO Penalties: Search engines penalize websites infected with malware, pushing them down in search results. This can significantly impact your website’s traffic and visibility.
- Visitor Redirection: Hackers can use malware to redirect visitors to malicious websites that steal information or spread further malware. This not only frustrates your visitors but can also damage your brand image.
Taking Back Control: Reputable Security Scanners
Fortunately, you don’t have to live in fear of malware. Several security scanners can identify and remove malicious code from your WordPress website. Here are some reputable options to consider:
Free Scanners:
- Sucuri SiteCheck: This free scanner provides a basic health report, highlighting malware, outdated software, and suspicious activity.
- Wordfence Security: The free version of Wordfence offers basic malware scanning and firewall protection.
Premium Scanners:
- Sucuri Security: The premium version offers more in-depth scans, website hardening recommendations, and ongoing monitoring.
- Wordfence Premium: Provides advanced malware detection, real-time threat defense, and security reports.
These scanners typically offer user-friendly interfaces that guide you through the scanning process. Once a scan is complete, you’ll receive a report detailing any identified threats.
Interpreting the Results and Taking Action
Scan results can be technical, but most scanners provide explanations and remediation steps. Here’s a simplified approach:
- Malware Detected: The report will likely identify infected files and provide instructions on how to remove them. This may involve manually deleting files or using the scanner’s built-in removal tool.
- Outdated Software: The scanner might identify outdated plugins or themes with known vulnerabilities. Update these immediately to the latest versions.
- Suspicious Activity: The report may flag suspicious code or activity. If you’re unsure about something, consult a security professional for further analysis.
Remember: Back up your website before making any significant changes, especially if malware removal is involved.
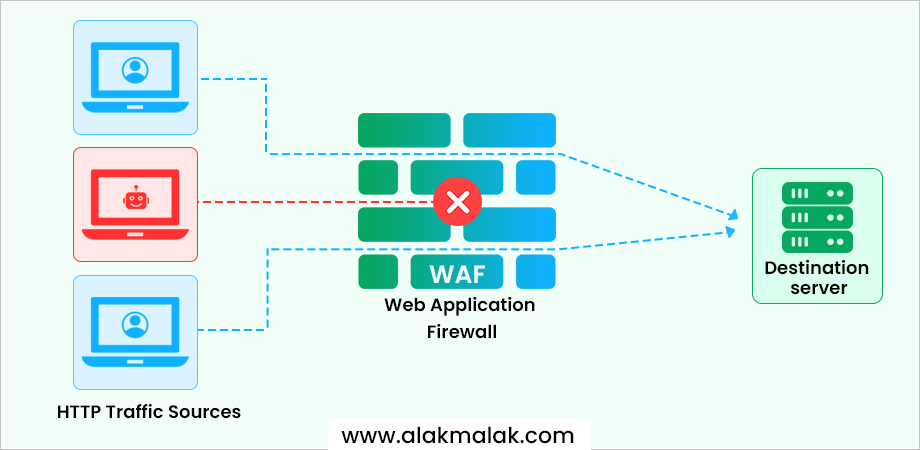
5. Set up a WordPress Firewall
A web application firewall (WAF) is a security solution that acts as a protective barrier between a website and the internet. Its primary function is to monitor and filter incoming traffic, identifying and blocking potential threats before they can reach the website. WAFs analyze each request for patterns and signatures that indicate malicious activity, such as SQL injection attacks, cross-site scripting (XSS), and other common web application vulnerabilities.
Benefits of using a security plugin with built-in firewall functionality:
- Convenience: Instead of configuring a separate WAF solution, the firewall is integrated directly into the WordPress environment, simplifying the setup and management process.
- Targeted Protection: These plugins are designed specifically to address common WordPress threats and vulnerabilities, providing targeted protection tailored to the platform.
- Automatic Updates: As new threats emerge, the plugin developers can quickly release updates to strengthen the firewall rules and keep websites secure.
- Additional Security Features: Many security plugins bundle firewall protection with other essential features like malware scanning, brute force attack prevention, and security hardening.
How to configure basic firewall rules to protect against common threats
- Enable the firewall and activate the default ruleset, which typically includes protection against common threats like SQL injection, XSS, and file inclusion attacks.
- Configure IP address blocking to prevent access from known malicious IP addresses or ranges.
- Set up rate limiting to restrict the number of requests from a single IP within a specific timeframe, mitigating brute force and DDoS attacks.
- Customize allowed/blocked HTTP methods and request types based on your website’s requirements.
- Regularly review and update the firewall rules to address emerging threats and vulnerabilities.
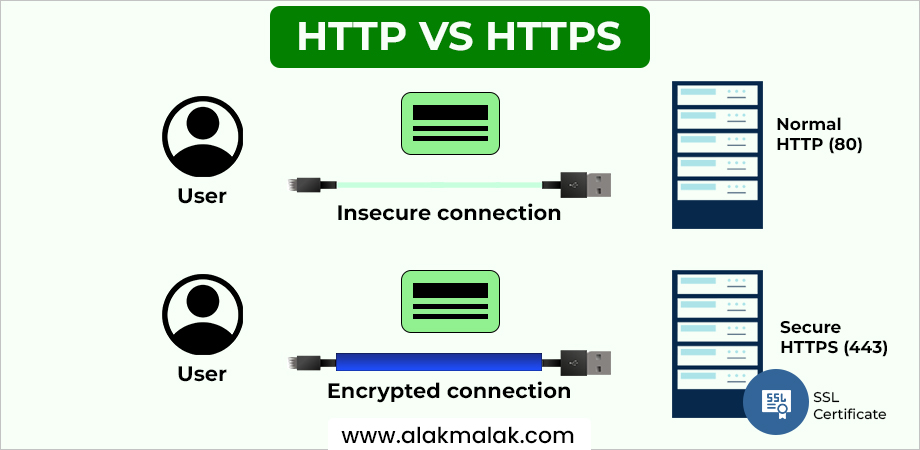
6. Enable SSL/HTTPS
In today’s digital landscape, securing communication between your website and visitors is paramount. This is where SSL/HTTPS comes into play. Let’s explore how this technology safeguards data and bolsters user trust in your WordPress website.
SSL/HTTPS: Encryption for a Secure Connection
Imagine a secure tunnel protecting sensitive information as it travels between your website and visitors. That’s essentially what SSL (Secure Sockets Layer) and its successor, HTTPS (Hypertext Transfer Protocol Secure), achieve.
Here’s how it works:
- Encryption: When a visitor accesses your website with SSL/HTTPS enabled, the communication channel is encrypted. This scrambles data like login credentials, credit card details, or contact form submissions, making it unreadable to anyone who might intercept it.
- Data Integrity: SSL/HTTPS ensures data remains unaltered during transmission. This prevents hackers from tampering with information sent between your website and visitors.
By implementing SSL/HTTPS, you demonstrate a commitment to data security, fostering trust with your visitors and protecting them from online threats.
Getting Your SSL Certificate: Securing Your Website
Obtaining an SSL certificate is a straightforward process. Here’s a basic overview:
- Free vs. Paid Certificates: Many web hosting providers offer free SSL certificates with their plans. These are sufficient for basic security needs. Paid certificates offer additional benefits like increased validation levels and customer support.
- Installation: The installation process can vary depending on your hosting provider. They typically offer instructions or support to help you install the certificate on your WordPress website.
- Resources: Let’s Encrypt is a popular provider offering free SSL certificates. Additionally, your web hosting provider’s documentation can guide you through the specific steps for obtaining and installing an SSL certificate on your WordPress site.
7. Remove Unused WordPress Plugins and Themes
Your WordPress website is a powerful tool, but it requires constant vigilance to maintain its security. One often-overlooked area is the collection of plugins and themes you have installed. Let’s explore why keeping only actively maintained and necessary WordPress plugins is crucial for safeguarding your website.
Outdated or Inactive Plugins/Themes: Open Doors for Hackers
Imagine leaving a spare key under your doormat – that’s essentially what keeping unused or outdated plugins and themes on your website does. These can create security vulnerabilities that hackers can exploit to gain access to your website.
Here’s why:
- Unpatched Security Holes: Developers regularly patch vulnerabilities in their plugins. Outdated plugins lack these vital security fixes, leaving them susceptible to known exploits. Hackers can leverage these vulnerabilities to inject malware, steal data, or take control of your website.
- Compatibility Issues: Outdated plugins might not be compatible with the latest version of WordPress, leading to conflicts and potential security gaps.
- Inactive Threats: Inactive plugins still reside on your server, and some might have inherent vulnerabilities. Even if not actively used, they can pose a security risk.
By keeping only actively maintained and necessary plugins, you minimize the attack surface for hackers and ensure your website benefits from the latest security updates.
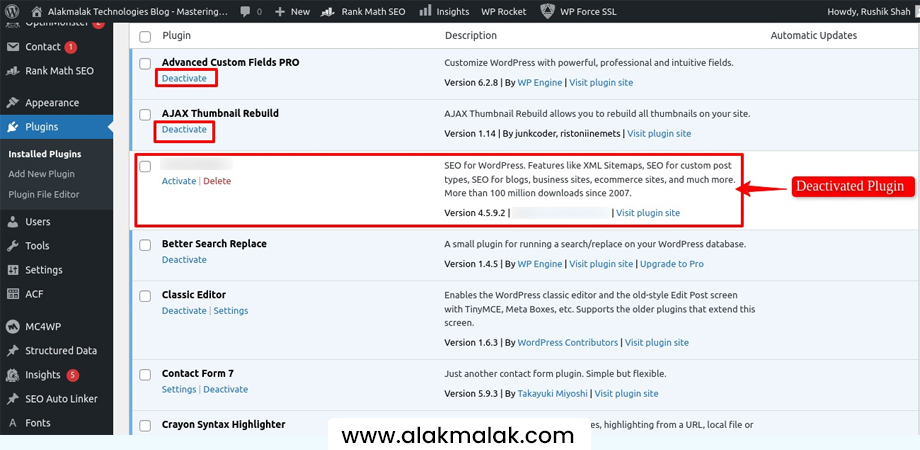
Cleaning Up Your WordPress Dashboard: A Safe Removal Process
Removing unused plugins and themes is a simple process within your WordPress dashboard:
- Navigate to Plugins: Go to the “Plugins” section in your WordPress dashboard.
- Identify Unused Plugins: Here, you’ll see a list of all installed plugins, including active and inactive ones. Identify plugins you no longer use.
- Deactivate and Delete: Click “Deactivate” for the chosen plugin, then click “Delete” to remove it completely from your server. Repeat this process for any other unused plugins.
Theme Removal: Follow a similar process by navigating to “Appearance” > “Themes” and deleting any unused themes.
Remember: Always backup your website before making significant changes.
8. Implement Downtime Monitoring
The importance of being notified if your website goes offline unexpectedly:
Websites can go offline unexpectedly due to various reasons, including hacking attempts, server issues, or hardware failures. If your website is offline, it means your business is essentially closed, leading to potential revenue loss, damage to your brand reputation, and dissatisfied customers. Being notified promptly when your website goes down allows you to take immediate action and minimize the impact.
Recommend free or paid downtime monitoring services and their benefits.
To ensure you’re promptly notified of any website downtime, it’s recommended to use a downtime monitoring service. These services continuously monitor your website’s availability and alert you if it becomes inaccessible. Here are some popular options:
Free Options:
- UptimeRobot: Offers free website monitoring with email and push notifications.
- Pingdom: Provides free monitoring for one website with basic alerting features.
Paid Options:
- StatusCake: Offers advanced monitoring and alerting features, including SMS notifications and integrations with popular communication tools.
- Uptime.com: Provides comprehensive uptime monitoring, performance monitoring, and detailed reporting capabilities.
The benefits of using a downtime monitoring service include:
- Immediate awareness of website outages or performance issues.
- Ability to quickly investigate and resolve the root cause of downtime.
- Monitoring from multiple global locations for comprehensive coverage.
- Historical uptime data and reporting for analysis and optimization.
How Downtime Monitoring Services Can Alert You of Potential Security Incidents:
Downtime monitoring services can serve as an early warning system for potential security incidents. If your website suddenly goes offline due to a hacking attempt or a distributed denial-of-service (DDoS) attack, the monitoring service will promptly notify you. This early notification allows you to investigate the issue, implement countermeasures, and potentially prevent further damage or data breaches.
Example: According to Cloudflare’s DDoS Attack Trends Report, the number of DDoS attacks increased by 175% in 2022 compared to 2021, highlighting the importance of proactive monitoring and security measures.
9. Add Security Headers
Imagine silent sentries guarding your website’s communication channels. That’s essentially what security headers do. They are directives sent by your web server to a user’s browser, instructing it on how to handle data securely. These headers operate behind the scenes, fortifying your website’s defenses without impacting user experience.
Here’s how to protect user data:
- Mitigating Common Attacks: Security headers can help prevent specific attacks like Cross-Site Scripting (XSS) or clickjacking. By dictating how the browser handles scripts and resources, they make it more difficult for hackers to inject malicious code or trick users into performing unintended actions.
- Data Protection: Certain security headers can restrict how data is accessed or stored by the browser, further safeguarding user information.
Simplifying Security with Plugins
Implementing security headers manually can be complex. Fortunately, many WordPress security plugins automate this process. These plugins configure essential security headers on your website, saving you time and technical expertise.
Optional: Advanced Security Headers for Tech-Savvy Users
For users comfortable with deeper technical configurations, some security headers offer granular control. For instance, Content Security Policy (CSP) allows you to define which resources (scripts, images, etc.) are allowed to load on your website. This can significantly reduce the risk of XSS attacks by preventing unauthorized scripts from executing.
Remember: While CSP offers advanced protection, it requires careful configuration to avoid unintended website functionality issues.
10. Set up Daily Backups
Securing a WordPress website from hackers is crucial for protecting your content, user data, and reputation. Among the various security measures, setting up daily backups stands out as a foundational step. Here’s why regular backups are essential and how you can implement them effectively.
The Importance of Regular Backups for Disaster Recovery
Regular backups act as a safety net in the event of a security breach. If hackers manage to compromise your site, having a recent backup means you can restore your site quickly, minimizing downtime and data loss. It’s not just about countering attacks; backups are also invaluable for recovering from accidental deletions, updates gone wrong, or server failures. In essence, daily backups ensure business continuity by providing a fallback option that can be the difference between a minor hiccup and a major catastrophe.
Recommended Backup Plugins and Web Host Options
Fortunately, WordPress users have access to several reliable backup solutions. Popular plugins like UpdraftPlus, VaultPress (part of Jetpack), and BackupBuddy offer automated backup capabilities, easy restoration, and secure off-site storage options. These plugins allow you to schedule daily backups without manual intervention, ensuring that your site is backed up consistently.
Besides plugins, many web hosting providers offer backup services, either included in their hosting packages or as an add-on. These host-provided backups can be incredibly convenient, offering deep integration with your server environment and possibly faster restoration times.
Scheduling Automatic Backups and Secure Off-site Storage
Setting up automatic backups is straightforward with the right plugin or host service:
- Choose a backup solution that meets your needs in terms of storage space, frequency, and price.
- Schedule your backups to occur daily, preferably during low-traffic hours to minimize impact on site performance.
- Opt for off-site storage solutions like Amazon S3, Google Drive, or Dropbox. Storing backups off-site ensures they’re safe even if your server is compromised or suffers a hardware failure.
Ensure that your backup solution encrypts the backup data for an extra layer of security during transfer and storage.
Conclusion:
In today’s digital landscape, safeguarding your WordPress website is paramount. This guide has equipped you with essential strategies to combat cyber threats. Remember, security is an ongoing process, but by implementing these steps, you’ve built a robust defense system:
- Fortify logins: Utilize strong passwords, limit login attempts, and leverage security plugins.
- Scan for vulnerabilities: Regularly scan your website for malware and outdated software.
- Add a firewall: Implement a WordPress firewall to filter out malicious traffic.
- Enable SSL/HTTPS: Encrypt communication between your website and visitors.
- Clean up your site: Remove unused plugins and themes to minimize vulnerabilities.
- Set up security headers: Utilize security headers to bolster website defenses.
- Back up daily: Create a daily backup routine to ensure a quick recovery in case of emergencies.
By following these practices, you’ve significantly enhanced your website’s security posture. Feel free to reach out for a consultation, or visit our website to learn more about our WordPress security solutions. We’re here to help you create a safe and secure online presence.
- hire dedicated php developer india
- hire dedicated php programmer india
- Professional Wordpress Development
- Securing a WordPress Website from Hackers

 By: Rushik Shah
By: Rushik Shah