In a world where our lives are increasingly intertwined with technology, the security of our digital assets has become paramount. Nowhere is this more evident than in the realm of Android application development company. With over 2.8 million apps available on the Google Play Store as of 2021, the need for robust security measures for Android application development cannot be overstated.
Imagine this: You’ve just downloaded a new app on your Android device, excited to explore its features. Little do you know, lurking behind its shiny interface lies a vulnerability waiting to be exploited by malicious actors. Unfortunately, this scenario is not uncommon, as cyber threats continue to evolve and target unsuspecting users through vulnerable apps.
This is where our blog post comes in. We aim to shed light on the importance of implementing top-notch security measures during Android application development. From encryption protocols to secure coding practices, we’ll delve into the tips and techniques that can safeguard your app and its users from potential security breaches.
As an experienced Mobile application developer with over 18 years in the industry, I’ve seen firsthand the consequences of neglecting security measures. From data breaches to malware attacks, the risks are real and the impact can be devastating.
So, let’s embark on this journey to fortify your Android applications and elevate your expertise in the realm of digital security.
Top Security Measures for Android Application Development

Now, let’s have a look at the security measures for android application development to avoid becoming a victim:-
1. Protecting Data in Transit
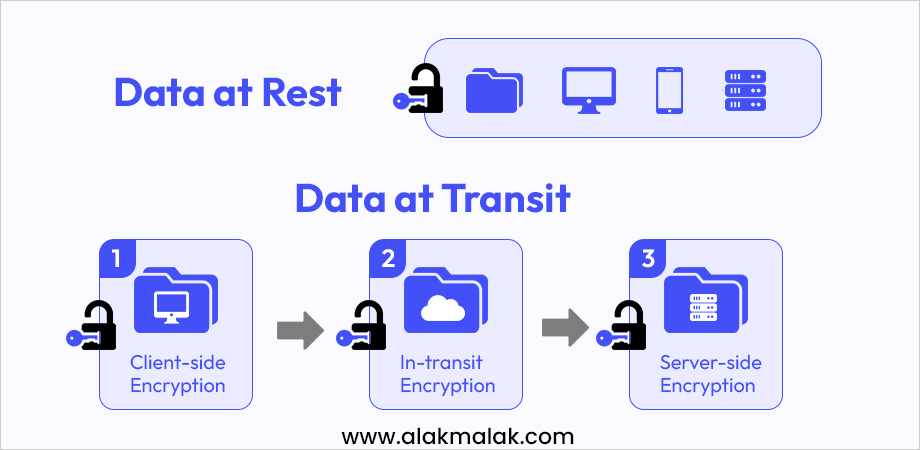
One of the most critical aspects of secure Android app development is protecting data while it’s traveling between your app and the server. This section dives into the importance of encrypting user data, specifically passwords and financial information, before transmission.
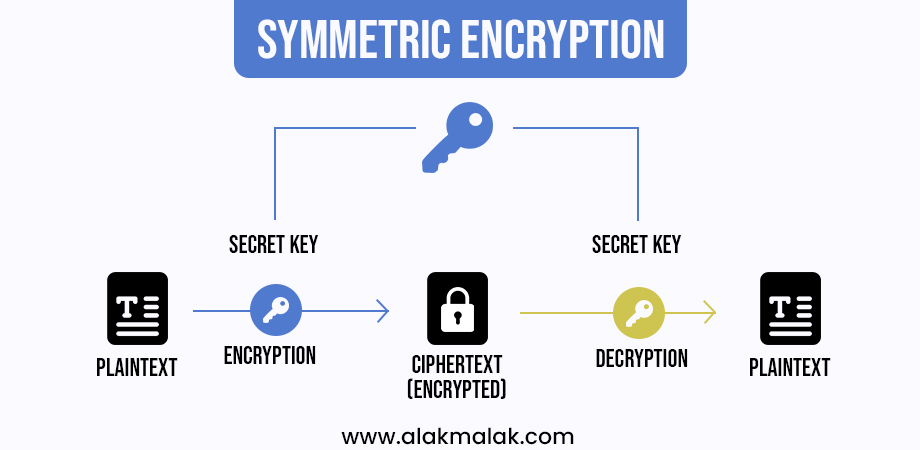
Encryption: Scrambling Data for Enhanced Security
Imagine sending a secret message to a friend. Normally, anyone who intercepts the message can read it. Encryption acts like a scrambling machine, transforming your message into an unreadable code. Only the intended recipient, possessing the decryption key, can unscramble the message back to its original form.
In the context of your app, encryption protects user data in transit. When a user enters their password or financial information, the app encrypts this data using a strong algorithm like AES (Advanced Encryption Standard). Even if an attacker intercepts this data during transmission, it appears as gibberish without the decryption key, rendering it useless.
Symmetric vs. Asymmetric Encryption: A Balancing Act
There are two main types of encryption used for securing data: symmetric and asymmetric.
- Symmetric Encryption: This method uses a single secret key for both encryption and decryption. It’s faster and ideal for large amounts of data, but key distribution and management become a challenge.
- Asymmetric Encryption: This approach utilizes a public-key pair: a public key for encryption and a private key for decryption. Anyone can encrypt data with the public key, but only the owner of the private key can decrypt it. This is more secure for key exchange but can be slower.
For data in transit, symmetric encryption is often preferred due to its speed advantage. However, some apps might employ a combination of both methods for added security.
Example: A recent study by IBM found that the average cost of a data breach in 2023 was a staggering $4.35 million.
2. Secure The Server

When developing Android applications, securing the backend server that stores user data is just as crucial as protecting the data in transit. Cybercriminals often target server-side vulnerabilities to gain unauthorized access to sensitive information, making it essential for Android app developers to prioritize server-side security measures.
Importance of Securing the Backend Server:
The server-side is the backbone of any Android application, as it is responsible for storing and managing user data. If the server is compromised, it can lead to a devastating data breach, exposing sensitive user information such as login credentials, financial details, and personal identifiable data. By ensuring the security of the backend server, Android app developers can safeguard their users’ data and maintain trust in their application.
Common Server-side Security Measures:
Firewalls: These act as gatekeepers, filtering incoming and outgoing traffic based on predefined security rules. They can block malicious attempts to access the server.
Intrusion Detection Systems (IDS): These systems continuously monitor server activity for suspicious behavior that might indicate an attack. They can trigger alerts or automatically take steps to mitigate threats.
Access Controls: This involves defining user permissions and access levels. Only authorized personnel should be able to access sensitive data, and their access should be logged and monitored.
Importance of Keeping Server Software Updated:
Just like your Android app, server software requires regular updates and security patches. These patches address newly discovered vulnerabilities that attackers might exploit. Keeping your server software up-to-date significantly reduces the risk of successful breaches.
By implementing a layered security approach with firewalls, intrusion detection, access controls, and regular patching, you create a formidable defense system for your server. This ensures user data remains secure within its digital fortress. Remember, server security is an ongoing battle, so staying vigilant and adapting to new threats is vital.
3. Use HTTPS

When building a secure Android application, ensuring safe communication between your app and the server is paramount. This is where HTTPS comes in, utilizing SSL/TLS certificates to establish a secure connection.
HTTPS: The Secure Delivery Channel
Think of HTTPS as an encrypted tunnel between your app and the server. Unlike regular HTTP, HTTPS encrypts all communication, scrambling data using strong algorithms. This makes it unreadable for anyone eavesdropping on the network traffic.
The Magic of SSL/TLS Certificates:
Imagine two friends communicating with secret codes. SSL/TLS certificates act like these codes, enabling secure communication between your app and the server. Here’s how it works:
- The Handshake: When your app connects to the server using HTTPS, a handshake occurs. The server sends its SSL/TLS certificate containing its public key and identity information.
- Certificate Validation: Your app verifies the certificate’s authenticity. It checks if it’s issued by a trusted certificate authority (like a digital security company) and ensures it matches the server it claims to represent.
- Secret Key Exchange: If validation succeeds, your app generates a temporary secret key. This key is encrypted using the server’s public key from the certificate and sent back to the server. Only the server’s private key (not included in the certificate) can decrypt this, establishing a shared secret key for the session.
- Encrypted Communication: Now, all data exchanged between your app and the server gets encrypted with the shared secret key, making it unintelligible to anyone intercepting it.
Building User Trust: Certificate Validation
The certificate validation step plays a crucial role in building user trust. It assures users that they’re communicating with the legitimate server and not a disguised attacker. Seeing a valid certificate reflected by a lock icon in the browser bar provides users with peace of mind.
By leveraging HTTPS with SSL/TLS certificates, you create a secure communication channel, safeguarding user data from prying eyes and potential tampering. This not only protects sensitive information but also fosters user confidence in your app.
4. Encrypt the Data Before Making the API call
An extra layer of security for user data goes beyond securing the channel with HTTPS. It’s equally important to encrypt the data itself before it even leaves the app. This adds another hurdle for attackers who might intercept data during transmission.
Encrypt Data at the Application Layer
Imagine a locked briefcase containing your valuables. Now, imagine placing each valuable inside a separate, smaller, locked box before putting them all in the briefcase. This is analogous to encrypting data within the app before sending it via an API call. Even if someone manages to access the briefcase (intercept the data), the individual valuables (data points) remain encrypted and unusable.
Key Management with Android Keystore System
The Android Keystore System provides a secure way to generate and store encryption keys within the Android device’s hardware security module. This ensures strong key protection and eliminates the risk of keys being compromised by malware on the device.
Tokenization: A Shield for Sensitive Data
For highly sensitive data like credit card numbers, consider tokenization. This process replaces the actual data with a unique identifier, called a token. The server stores the token and uses it to reference the actual data securely. Even if an attacker intercepts the token, they cannot use it without the additional information stored on the server.
Example: A study by Verizon found that 61% of data breaches in 2023 involved stolen credentials. Encrypting data at the app level significantly reduces the value of stolen information for attackers, making your app a less attractive target.
5. Implement Regular Updates
Regular updates are crucial for maintaining a strong security posture.
Plugging the Gaps: Proactive Security Patching
Imagine tiny holes appearing in your app’s security wall. These holes represent vulnerabilities that attackers can exploit. Regular security updates act like patches, promptly addressing these vulnerabilities and ensuring your app remains secure.
A Developer’s Duty: Staying Ahead of Threats
The responsibility for fixing vulnerabilities lies with the app developer. Security researchers constantly discover new threats, and developers need to be proactive in identifying and patching vulnerabilities within their apps. This demonstrates a commitment to user safety and fosters trust.
Testing and Deploying Security Updates:
The process of releasing security updates involves thorough testing:
- Internal Testing: Developers first test the update to ensure it fixes the vulnerability without introducing new bugs or compatibility issues.
- Beta Testing: A limited group of users might test the update to gather feedback and identify any unforeseen problems.
- Public Release: Once testing is complete, the update is rolled out to all users through the Google Play Store.
By emphasizing the importance of regular security updates, the developer’s responsibility to address vulnerabilities, and the process of testing and deploying updates, Android app developers can demonstrate their commitment to user security and build trust within their user base.
6. Securing Network Communication
We’ve covered several crucial measures for securing network communication in your Android app:
- HTTPS with SSL/TLS Certificates: This encrypts all communication between your app and the server, safeguarding data from eavesdropping and tampering.
- Data Encryption at the App Level: Encrypting sensitive data before making API calls adds an extra layer of security, rendering it useless even if intercepted.
- API Security: Implementing strong access controls and authentication mechanisms for API calls ensures only authorized users can access data.
For developers seeking an even more robust approach, consider certificate pinning.
Certificate Pinning: Double-Checking Server Identity
Imagine verifying your friend’s identity not just by their voice but also by a secret code only the two of you know. Certificate pinning works similarly. It involves storing a trusted server certificate’s fingerprint within the app. During the HTTPS handshake, your app verifies if the server’s certificate matches the pinned fingerprint. If not, the connection is terminated, preventing man-in-the-middle attacks where attackers impersonate the legitimate server.
Example:
The Heartbleed bug of 2014 exposed a major vulnerability in OpenSSL, a widely used library for secure communication. Attackers could exploit this bug to steal sensitive data transmitted over HTTPS connections. While the bug itself has been patched, it highlights the importance of layered security measures like certificate pinning. Even if an attacker manages to compromise a certificate authority, certificate pinning can still prevent them from impersonating the server.
By implementing these advanced techniques alongside the previously mentioned measures, you can significantly strengthen your app’s network security posture. This demonstrates a deep understanding of security best practices and fosters trust with users who value their data privacy. Remember, staying updated on the latest threats and adopting new security measures is an ongoing process for developers.
7. Implement Code Obfuscation
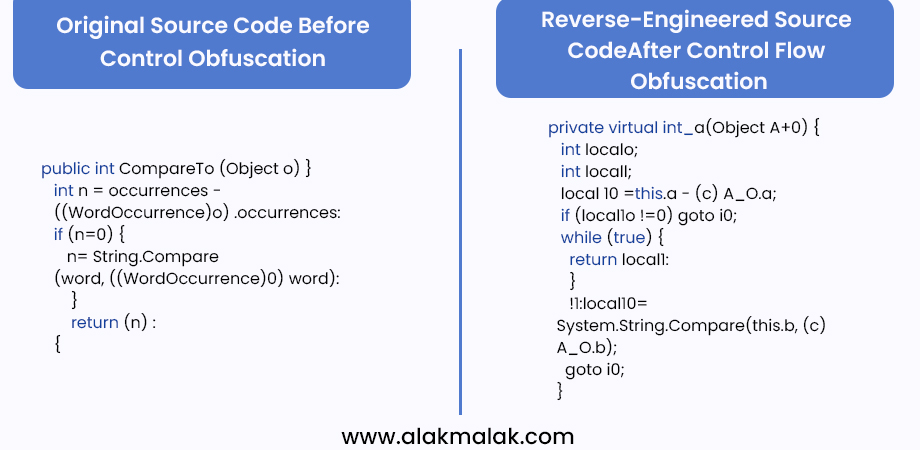
Code obfuscation can be a valuable tool in your Android app security arsenal. By scrambling your code, it makes it more difficult for attackers to understand how your app functions and potentially find vulnerabilities. However, it’s crucial to remember that obfuscation is not a magic shield – it shouldn’t be your sole security measure.
Beyond Obfuscation: Building a Secure Foundation
Imagine securing your house with just a slightly tinted window. While it might make it harder to see inside, a determined intruder could still break in. Obfuscation works similarly. It makes prying eyes work harder, but a skilled attacker with enough time and resources can often decipher obfuscated code.
True Security: A Multi-Layered Approach
The real key to a secure app lies in building a strong security foundation. This includes:
- Robust Encryption: Encrypting data at rest and in transit with strong algorithms like AES significantly reduces the value of stolen information even if attackers manage to bypass obfuscation.
- Secure Coding Practices: Following secure coding guidelines helps prevent common vulnerabilities that attackers can exploit, regardless of obfuscation.
- Regular Security Updates: Proactively patching vulnerabilities identified in your app and its libraries is essential for maintaining a strong security posture.
Obfuscation as a Complementary Measure:
Consider obfuscation as an additional layer of security, making it more difficult for attackers to exploit vulnerabilities. Here’s an analogy: Imagine your house now has tinted windows, a high fence, and a guard dog. While someone might still attempt a break-in, the additional layers significantly deter them.
By combining obfuscation with robust encryption, secure coding practices, and regular updates, you create a well-rounded security strategy for your Android app. This layered approach deters attackers and fosters trust with users who value their data privacy. Remember, security is an ongoing process, so stay updated on the latest threats and adapt your strategies accordingly.
Conclusion:
In this blog, we’ve covered the top security measures for Android application development, from encrypting data in transit to implementing regular updates and leveraging code obfuscation. These best practices are crucial for safeguarding user data and building trust.
Remember, security is an ongoing process. Stay vigilant, monitor threats, and continuously improve your app’s security posture.
If you’re an Android developer seeking to enhance your app’s security, our experts are here to help. Contact us today to schedule a consultation and take the first step towards a more secure Android app.

 By: Rushik Shah
By: Rushik Shah


